
Criminals are using increasingly sophisticated techniques and technology to defraud contact centres.
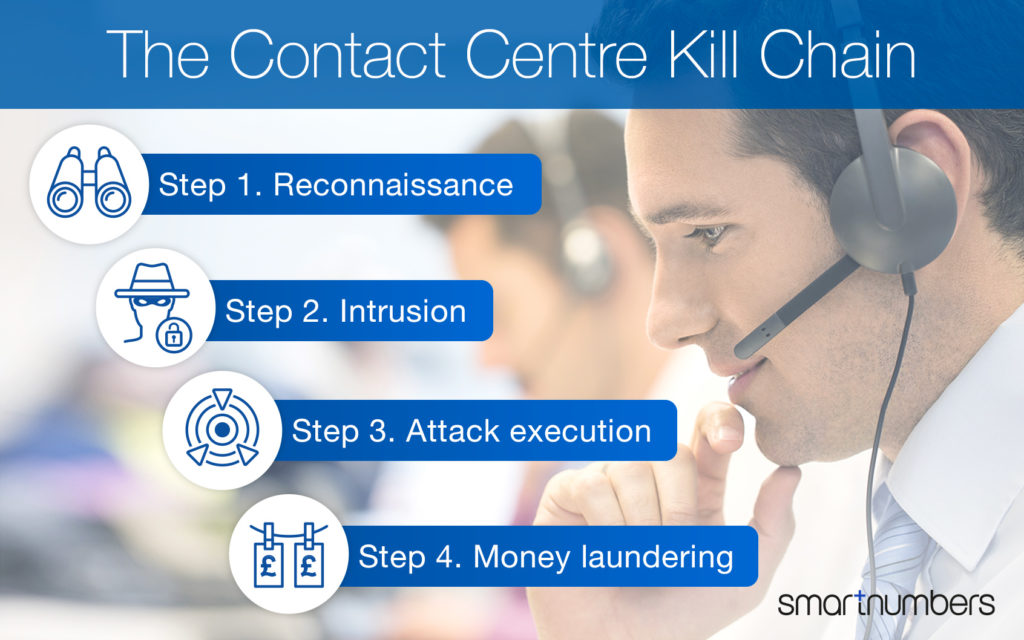
While fraudsters vary their tactics and are consistently modifying their approach, attacks follow a similar phased approach we call the Contact Centre Kill Chain, similar to the phased approach criminals attack the cyber channel in the Cyber Kill Chain.
The Smartumbers service gives you the advanced tools you need to prevent attacks. Using Call DNATM technology, Smartnumbers identifies suspicious callers, pre-answer, to provide the visibility and control during attacks that you need to enhance the defence of your contact centre.
Step 1. Reconnaissance
Attackers activity: Fraudsters conduct research to understand how to execute their attack. To gather static data required to overcome ID&V processes they acquire or harvest personal data from genuine customers or from the dark web. The attackers probe the IVR for verification of stolen information and to identify the optimal time for the attack.
The Smartnumbers defence – Fraudsters exploit IVR capabilities to gather further information such as balance checking or validation of a card’s CVV. The Smartnumbers service secures your IVR by identifying suspicious callers, such as repeat callers, and redirects them for additional scrutiny before they have the opportunity for IVR inquisition.
Step 2. Intrusion
Attackers activity: This is where the fraudster puts the static and dynamic data they have gathered into malicious use and set the foundations for executing the fraud. The fraudster breaks into the account and sets-up new payees, asks for password resets, change the account’s address or set-up new accounts.
The Smartnumbers defence – This is a critical point of the attack that you must prevent to defend against the attack. The Smartnumbers service examines the Call DNATM to identify suspicious callers, such as spoofed numbers, to prevent them from being allowed to complete sensitive tasks and redirecting them for additional scrutiny.
Step 3. Attack execution
Attackers activity: This is where the fraudster activates their attack, often known as the cashout stage. This is where the fraudster orders a new device on their contract, requests a money transfer to a different bank account or changing the delivery of high-value goods.
The Smartnumbers defence: This is the last chance to defend against fraud. By blocking suspicious callers from high-risk activities protects you from fraud while genuine customers receive a good customer experience.
Step 4. Money laundering
Attackers activity: Once the fraudster has cashed-out they need to clean the money before they can access cleared funds.
